Cyber threats are constantly changing, pressing alarming risks not only to big enterprises but also to small businesses. In the United States of America, the statistics are disturbing. For instance, according to an estimate the average loss for data theft is around 4 million dollars.
This blog will explain various security threats that US digital commerce businesses are facing and will focus on the preventive measures and response strategies against cyber threats.
Insight into Cybersecurity Threats to Businesses in the US
Cyber threats include a vast range of malicious activities designed to damage networks or computer systems. Some of the most prevalent cyber threats include ransomware attacks, phishing scams, data breaches, denial of service attacks, and insider threats.
They encrypt system files, making them inaccessible until a ransom is paid. Cyber threats can also deceive you to provide sensitive information and can get unauthorized access to your data. Moreover, threats can be from internal sources of an organization like mishandling of the company’s sensitive information.
Here are the details of the most common cybersecurity threats for retail businesses in the US:

1. Phishing Scams
Through phishing scams attackers trick individuals and companies to provide sensitive information. They act as a trustworthy entity to get information like passwords, financial data, or usernames. Moreover, these phishing scams can be in multiple forms such as social media messages, text messages, and emails.
Key Properties
Here are some key features of phishing scams discussed:
-
False Messages
Deceptive emails often contain urgent messages, provoking excitement or fear, and urging recipients to act quickly without verifying the authenticity of the source.
-
Bogus Links
Links attached with phishing emails may lead to fake websites, which are designed to acquire personal information. Hackers use certain tactics like URL spoofing to make fake links appear legitimate to trap users.
-
Spear Phishing
In spear phishing, cyber attackers generate personalized messages and send them to the target person or e-business. It becomes difficult to detect the malicious nature of the text, and eCommerce organizations get trapped this way.
2. Ransomware Attacks
Ransomware attacks are one of the most deceptive cybersecurity threats for e-businesses in the US. Such malware encrypts user’s files, keeps them on rendering and inaccessible, until a ransom is paid by the victim. Additionally, ransomware can be launched through malicious emails, compromised software, or suspicious downloads.
Key Properties
Key properties of ransomware attacks include:
-
Encryption
Once your system is attacked, the ransomware encrypts your files. Cybercriminals usually display a ransom note asking for payment in cryptocurrency.
-
Targeting
Large businesses are often targeted with hefty amounts in the US. Similarly, cybersecurity threats to small retail businesses in the US are also on rise, and they usually may lack the resources to protect themselves against cyber-attacks.
-
Results
In addition to ransom payments, e-organizations also bear the cost for system recovery, legal fees, and reputational damage after becoming victim to cyber intrusions.
3. Data Theft
Data theft is a term used when unauthorized individuals access and steal sensitive data of your company. Sensitive information includes customer records, intellectual property, or credit card numbers. There are multiple ways to initiate data theft such as social engineering, hacking, or exploiting vulnerabilities in eCommerce company’s software.
Key Properties
Some important features of data theft are here:
-
Hacking
For data theft, hackers mostly employ techniques like SQL injection, brute force attacks, or malware. Through such techniques, they can infiltrate your web system and steal critical information.
-
Social Engineering
Cybercriminals can also manipulate individuals in a business organization to share confidential information. They adopt ways comprising deceit and impersonation to steal crucial data of any organization.
-
Repercussions
Due to data theft, you can face multiple consequences including financial loss, legal penalties, and reputational damage. As clients lose trust in an organization that fails to protect their personal information.
4. DoS and DDoS Attacks
Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks focus to overwhelm a system, making it unavailable for the users. DoS attacks usually come from a single source however DDoS attacks include multiple compromised systems operating together to flood a target with online traffic.
Key Properties
Here we have some key properties of DoS and DDoS attacks:
-
Overloads
Attackers may use multiple methods to curate excessive digital traffic, including botnets to control the target system and carry out cybercrimes.
-
Targets
The most common targets of DoS and DDoS attacks are websites, web applications, and online services of a business in the US. A successful cyber-attack disrupts business operations resulting in client dissatisfaction and revenue loss.
-
Mitigation
It is quite difficult for an organization to mitigate DDoS attacks as they require investment in advanced security solutions. Moreover, mitigation is challenging due to the adaptation and investment in traffic management strategies.
5. Insider Threats
Insider threats originate from within the digital retail organization. Such threats often come from individuals or contractors, they may unintentionally or deliberately compromise sensitive information of any company. There are certain factors behind insider threats like negligence, lack of awareness, and malicious intent.
Key Properties
Some characteristics of insider threats are described here:
-
Types
Insider attacks can be broadly classified into two categories:
- Malicious Attacks: such as data sabotage
- Unintentional Threats: including accidental data leaks
-
Detection
To identify and mitigate insider threats, online businesses in the US can consider monitoring employee behavior and implementing security protocols, before cyber threat escalates.
The Impact of Cybersecurity Threats on US Enterprises
Cybersecurity threats impact online marketplaces in multiple ways in the US, including monetary losses, damaging a company’s reputation, drawing legal consequences, and causing operational disruptions in an organization’s workflow.
Let’s get into some details regarding the effects of cybersecurity threats on US enterprises:
1. Economic Loss
The instant impact of any cybersecurity threat can be notable, involving losses of hefty amounts in the form of ransom payments, potential fines from regulatory bodies, and recovery costs to hire experts for restoring encrypted systems. This would affect the cash flow and profitability margin of e-business owners.
2. Reputational Damage
Cybersecurity threats can cause a blow to a digital company’s reputation. When clients get to know that their personal data has been compromised, then their trust is reduced in the company. This can potentially lead to defaming the organization, loss of customers, and directly impacting the business revenue.
3. Legal Repercussions
Various data protection regulations are protecting US eCommerce firms such as California Consumer Privacy Act (CCPA) and General Data Protection Regulation (GDPR). If a company is unsuccessful in protecting consumer data, it may face legal consequences under protection regulations.
4. Operational Interruptions
Cyber-attacks can severely disrupt regular operations of a digital organization. For example, ransomware attacks can halt productivity by locking employees out of critical systems. This can damage all operations from customer service to supply chain management resulting in revenue losses for the web development companies.
Prevention Techniques for Cybersecurity Threats
A proactive approach is required for cyber-attack prevention in the US for web-based retailers. There are multiple strategies which can be opted for such as employee training, password policies, regular software and data updates, access control, and network security and audits.
Here are some methods discussed for cyber-attack prevention for US digital businesses:

1. Employee Training
Through regular training sessions, employees would be able to detect any phishing attempt or other security issues. Awareness can be raised among workers by conducting simulated phishing attacks during training.
2. Strong Password Policies
Encourage the implementation of complex passwords and password updates regularly. Moreover, especially for preventing cybersecurity threats to small businesses in the US install multi-factor authentication for accessing sensitive systems.
3. Updating Software
Regular updating of software and operating systems can fix the vulnerabilities in a company’s system which cybercriminals try to exploit. Moreover, new security features enhancement through frequent updates is crucial to maintain a cybersecurity posture.
4. Regular Data Backup
You should backup your important data to an offsite location or to cloud. This would help to reduce data loss of your business in the US due to cyber-attacks. Also, regularly test your backup systems to ensure the backup integrity and to identify any loopholes in the system.
5. Network security
To ensure network security, install dynamic firewalls. They would assist in preventing unauthorized access to your web business site. For data breach protection and to identify these breaches you can use intrusion detection systems (IDS) like Snort or Zeek to monitor online traffic.
6. Access Control
To tackle phishing scams, implement role-based access controls (RBAC). Through these RBAC controls you can prevent any attempt at acquiring sensitive data. This would give access to the workers as per their job roles. Moreover, conduct regular reviews and remove employees who are not part of the organization anymore.
7. Security Audits
Conduct internal assessments and regular external audits of your systems to measure the effectiveness of the business’s security policies. Regular audits of user and admin accounts are crucial for preventing ransomware attacks, by limiting hostile access to your digital store.
Response Approaches to Cybersecurity Threats
A well-defined response plan is vital for tackling cyber incidents and having a post cyber-attack recovery. Some key approaches to minimize the damage caused by cyber-attacks include instant containment of attack, situation analysis, reporting to stakeholders, record maintenance, and post incident reviews.
Here are some key response approaches to cybersecurity attacks:
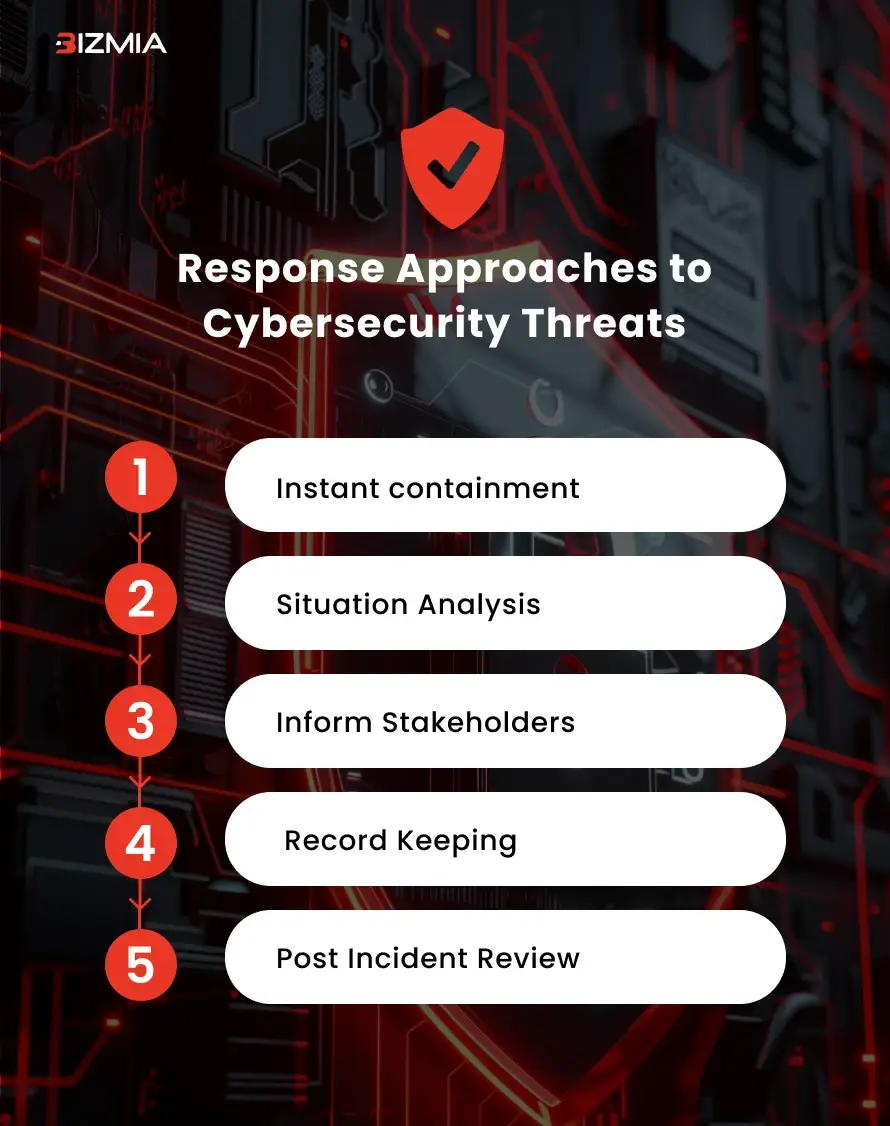
1. Instant Containment
The objective for instant containment of security attack is to prevent further damage and to halt unaffected areas of your digital business’s system. For this approach your priority should be isolation of the affected systems. You can disable user accounts, disconnect infected devices from the network, and then implement firewall settings to block malicious traffic.
2. Situation Analysis
Situation analysis is done to observe the nature and scope of cyber incidents. Start with the identification of threat vector, like how the threat occurred. Then assess the cyber-attack’s impact on business operations by checking logs and monitoring system behavior. Furthermore, risk assessment can assist in prioritizing response efforts.
3. Inform Stakeholders
To ensure transparency and trust in response approaches, inform the concerned parties about any cyber-attack on your system. You can start by developing a communication plan highlighting what information should be reported, to whom, and when. Moreover, make sure you timely inform the stakeholders, so that adequate measures can be taken to fix the issues that occurred due to cyber intrusions.
4. Record Keeping
Try to keep a record of all response actions in case of digital attacks. Maintain a detailed log of all response measures which you adopted. Also, preserve any evidence such as files, emails, or logs that is useful for forensic analysis of intrusion. Try to ensure legal compliance with your document as well.
5. Post Incident Review
Post incident review is crucial to conduct to identify all the lessons learned while tackling cyber intrusions. You can start this review by organizing a debriefing for all stakeholders. Then to identify vulnerabilities in security protocol conduct a root cause analysis, as per the findings of analysis update your response plans and strategies.
Let’s upscale your eCommerce game with Bizmia
Conclusion
With the digital transformation in eCommerce operations, the increase in cybersecurity threats is challenging for digital businesses in the United States. From ransomware attacks to insider attacks, the complexity of cyber intrusions requires comprehensive prevention and response measures. By implementing the dynamic preventive strategies as described in this blog from employee training to security audits, US e-businesses can adopt a proactive cybersecurity approach.
Moreover, a well-defined response plan including analysis, reviews, and reporting is crucial to minimize the impacts of digital attack at your retail business.
FAQs
1. What are the most common cybersecurity threats for US e-businesses today?
The most common cybersecurity threats for US e-businesses today include ransomware attacks demanding ransom for restoring your system access, and phishing scams getting sensitive information through malicious means. Data thefts in the form of unauthorized access to your sensitive data, DoS and DDoS attacks making system unavailable to users. This list also includes insider attacks on US online businesses from inside the organization.
2. How can small retail businesses adopt preventive measures for cybersecurity threats?
Small businesses can adopt several preventive measures to cease cybersecurity threats such as training employees by giving simulated threat situations, adopting strong password policies, by regularly updating software and data backups. Additionally, through network security and audits, and ensuring access control to relevant persons security threats can be prevented.
3. How can digital businesses deal with a ransomware attack?
To tackle ransomware attacks, digital businesses can focus on instant containment of digital attacks, situation analysis to observe nature of intrusion, and timely reporting to stakeholders. Moreover, record keeping for future reference, and post incident reviews are crucial to document all lessons learned during the responding process towards security attacks.
4. What are the prominent signs of a phishing scam?
Some prominent indicators of phishing scams include unsolicited messages and emails, generic greetings like “Dear Customer”, and suspicious links to fake websites. Phishing signs also include urgent calls to action, poor grammar, spelling and unprofessional language, and unexpected attachments with emails from unknown senders.












